In February 2016, Bangladesh Bank was the victim of a widely publicised cyberattack on its infrastructure, which was connected to SWIFT. Following the attack, SWIFT launched its Customer Security Programme to drive collaboration in the industry against cyberthreats. Three years on, how has it fared? Patrick Brusnahan writes
The quest for collaboration in cybersecurity continues. At the start of 2018, SWIFT aimed to increase its collaboration with key industry experts such as anti-virus vendors and incidentresponse teams.

Access deeper industry intelligence
Experience unmatched clarity with a single platform that combines unique data, AI, and human expertise.
SWIFT claims that these efforts resulted in the quick identification of financial institutions targeted by cybercriminals. Perhaps more significantly, it managed to do this before fraudulent transactions were sent.
In its report Three years on from Bangladesh: Tackling the adversaries, SWIFT examines trends observed between 2018 and 2019. These include tell-tale signs and how they become crucial in detecting and responding to attempted attacks.
Dries Watteyne, head of the cybersecurity incident-response team at SWIFT, wrote: “SWIFT’s threat intelligence sharing has highlighted the changes to cybercriminals’ tactics, techniques and procedures used in attempted attacks, enabling industry participants to understand, and respond to, the increasingly sophisticated nature of cyberthreats.
“It is encouraging that detection rates of attempted attacks are increasing, but we need to be mindful that malicious actors adapt rapidly. The industry must continuously strengthen and diversify its defences, investigate incidents and share information.”
US Tariffs are shifting - will you react or anticipate?
Don’t let policy changes catch you off guard. Stay proactive with real-time data and expert analysis.
By GlobalDataBrett Lancaster, head of customer security at SWIFT, added: “These cases show how SWIFT solutions, including our Daily Validation Reports tool, our Payment Controls Service and the gpi Stop and Recall facility, can all have real, positive impact. They also evidence the importance of implementing security controls, and of understanding and mitigating against cyber-risks presented by counterparties. This is why more and more customers are turning to SWIFT’s KYC Security Attestation utility to consume that information.”
Targets
SWIFT does not reveal who the main targets of cyberattacks are, but has narrowed it down to a few themes: in most cases, the financial institutions targeted are based in countries with a very high risk level on the Basel AML Country Corruption List.
Over the last 15 months, a large chunk of the attacks have targeted businesses in Africa, Central Asia, South East Asia and Latin America. In every case, however, the targets were smaller banks in terms of daily crossborder transactions.
In the vast majority of cases investigated, the graphical user interface was used to insert the fraudulent transaction. As a result, instructions would not have been present in payment back-office applications.
Therefore, it would have been detectable through the verification of end-of-day or start-of-day statement-reconciliation messages.

Amounts
Fraudsters are constantly performing a balancing act: the larger the fraudulent transaction attempted, the greater the reward, but also the greater chance that detection systems are triggered.
Since the Bangladesh Bank incident, SWIFT believes the amounts sent in individual fraudulent transactions have “evolved”.
Its report states: “Up until early 2018, we typically saw per transaction amounts of ten or tens of millions US dollars; however, since then, attackers have significantly reduced average per transaction amounts to between $0.25m and $2m – presumably to help avoid detection.”
However, fraudulent transaction amounts tended to be significantly higher than the “average” amounts sent in the prior 24 months.
Currencies
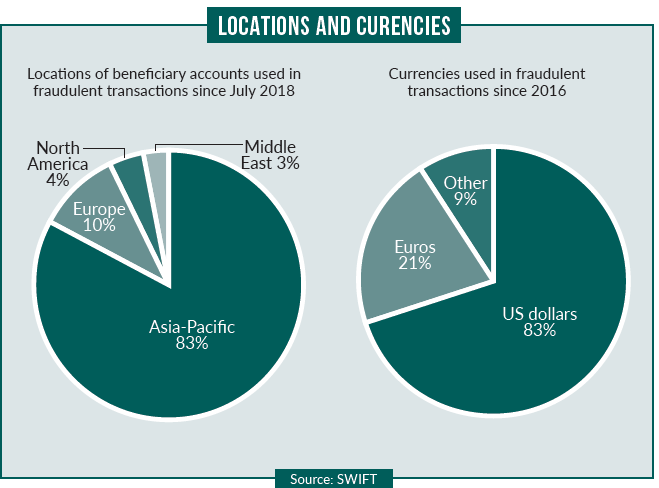
US dollars account for the majority of cross-border traffic; as a result, this was the currency most used in investigated incidents, accounting for close to 70% of fraudulent messages created since the Bangladesh Bank attack.
However, since the incident, there has been increased use of European currencies such as sterling and euros. In addition, a small number of Asia-Pacific currencies – mainly the yen and Hong Kong and Australian dollars – accounted for around 5%. Most beneficiaries of fraudulent transactions – some 83%, according to SWIFT – were based in Asia-Pacific.
The remaining 17% was split between Europe, the Middle East and North America. The report concludes: “The industry should continuously increase the strength and diversity of its defences, and ensure it understands the nature of the changing threat.
“This means being proactive in limiting criminal opportunities linked to systems and business practices. It means ensuring proper preparedness and understanding counterparty cyber-risk.”








